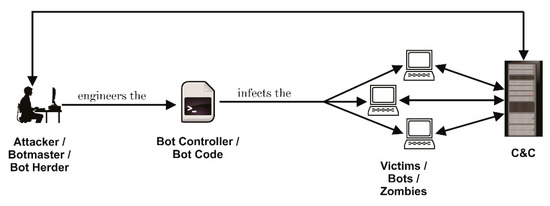
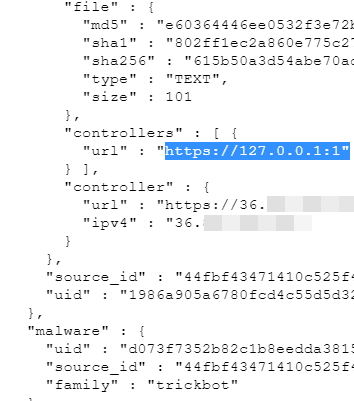
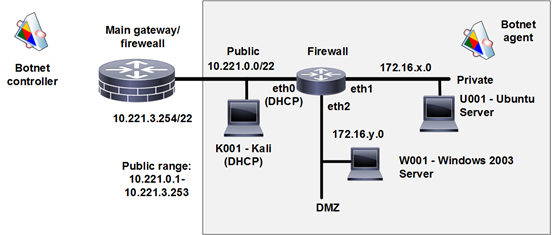
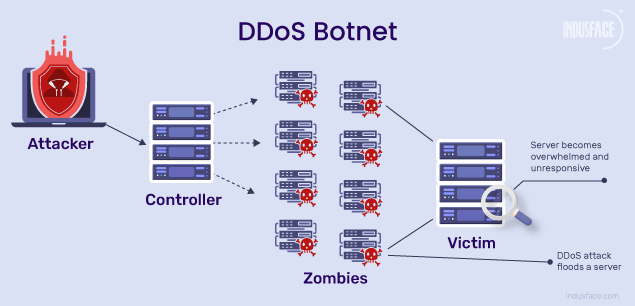
KV-botnet dirotta i router SOHO e le VPN: ecco le possibili misure di mitigazione - Cyber Security 360
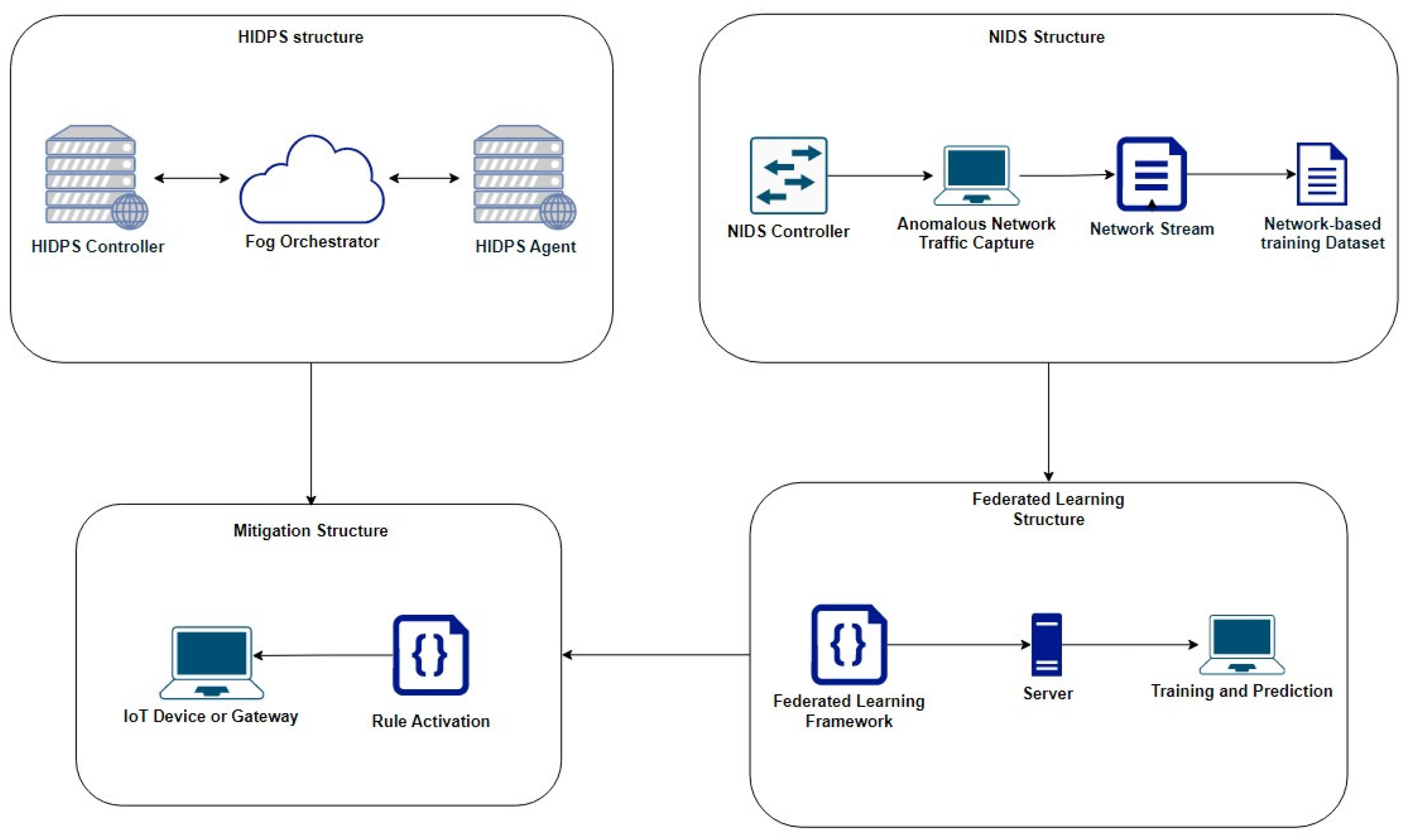
Sensors | Free Full-Text | Botnet Detection and Mitigation Model for IoT Networks Using Federated Learning

A novel botnet attack detection for IoT networks based on communication graphs | Cybersecurity | Full Text

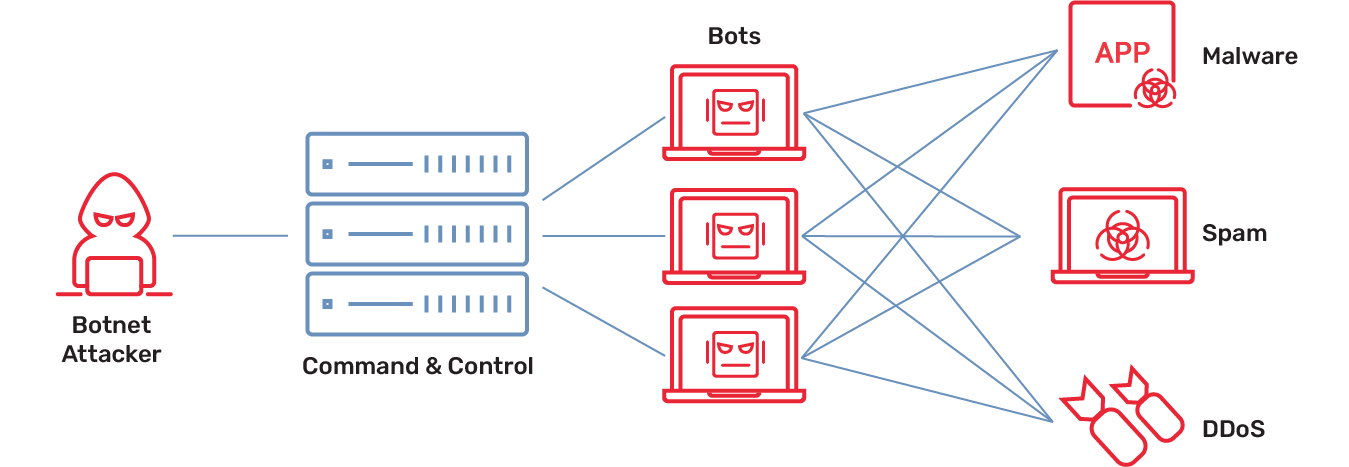
Fighting botnets with economic uncertainty - Li - 2011 - Security and Communication Networks - Wiley Online Library
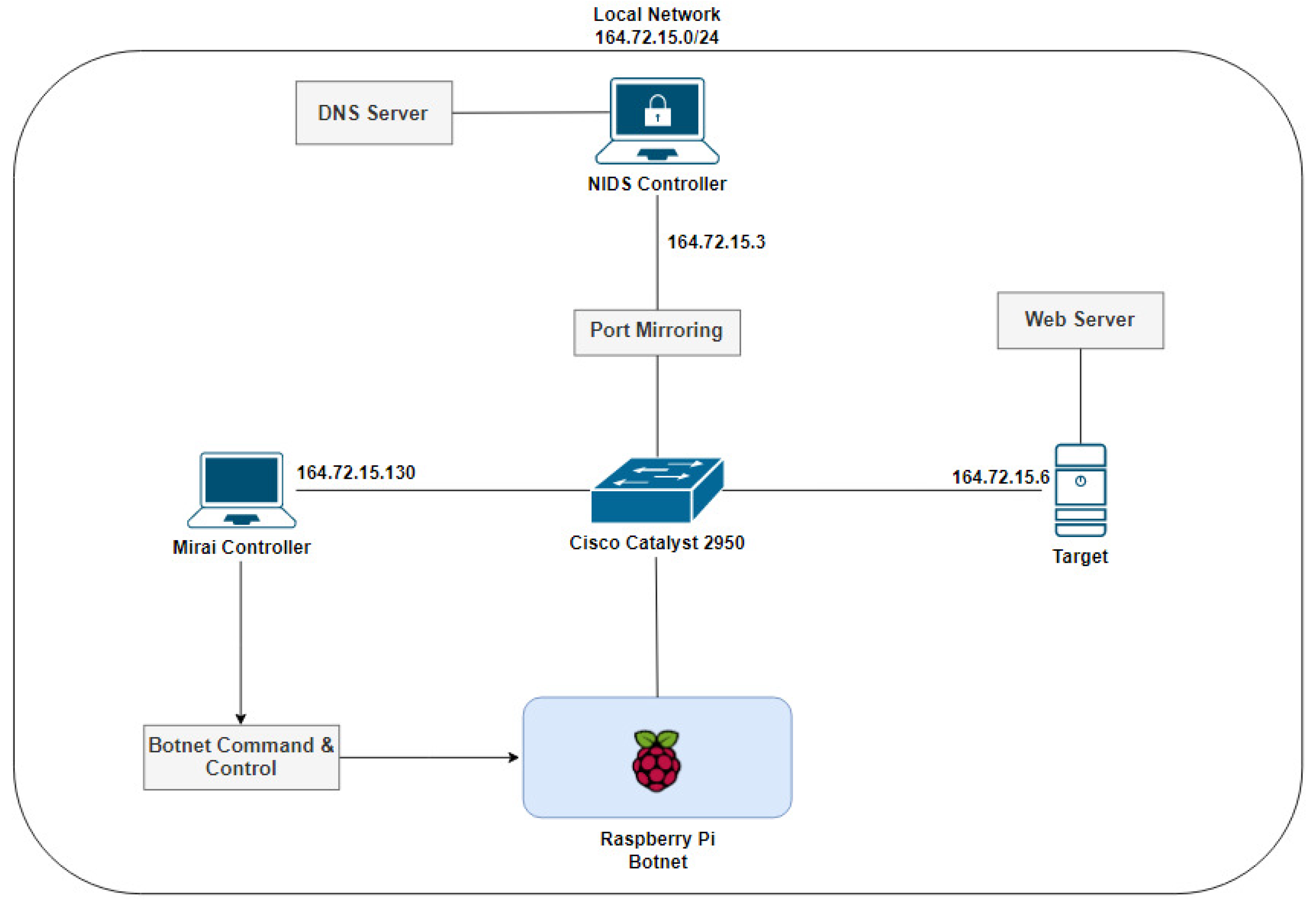
Sensors | Free Full-Text | Botnet Detection and Mitigation Model for IoT Networks Using Federated Learning

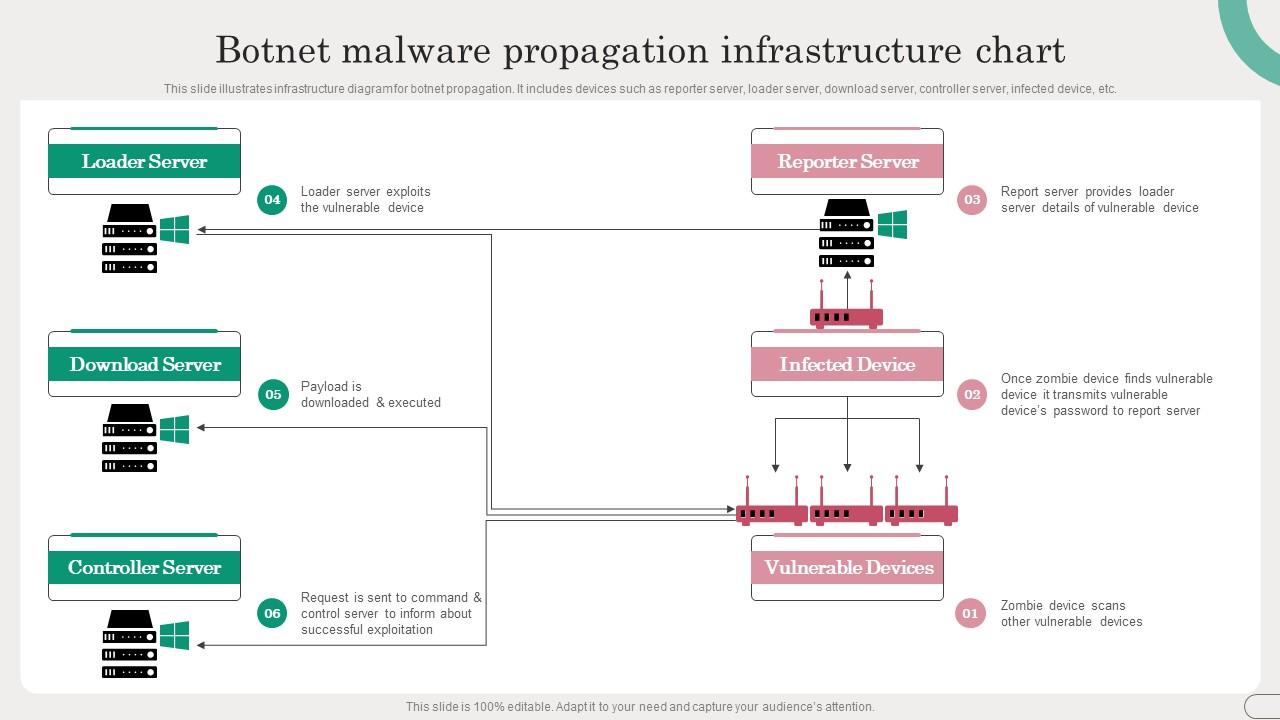
CyberKnow on X: "Apparently, Meris botnet is back and in its 3rd version will be able to infect IOT devices. This would increase the attack capability of the botnet. Apparently Meris botnet
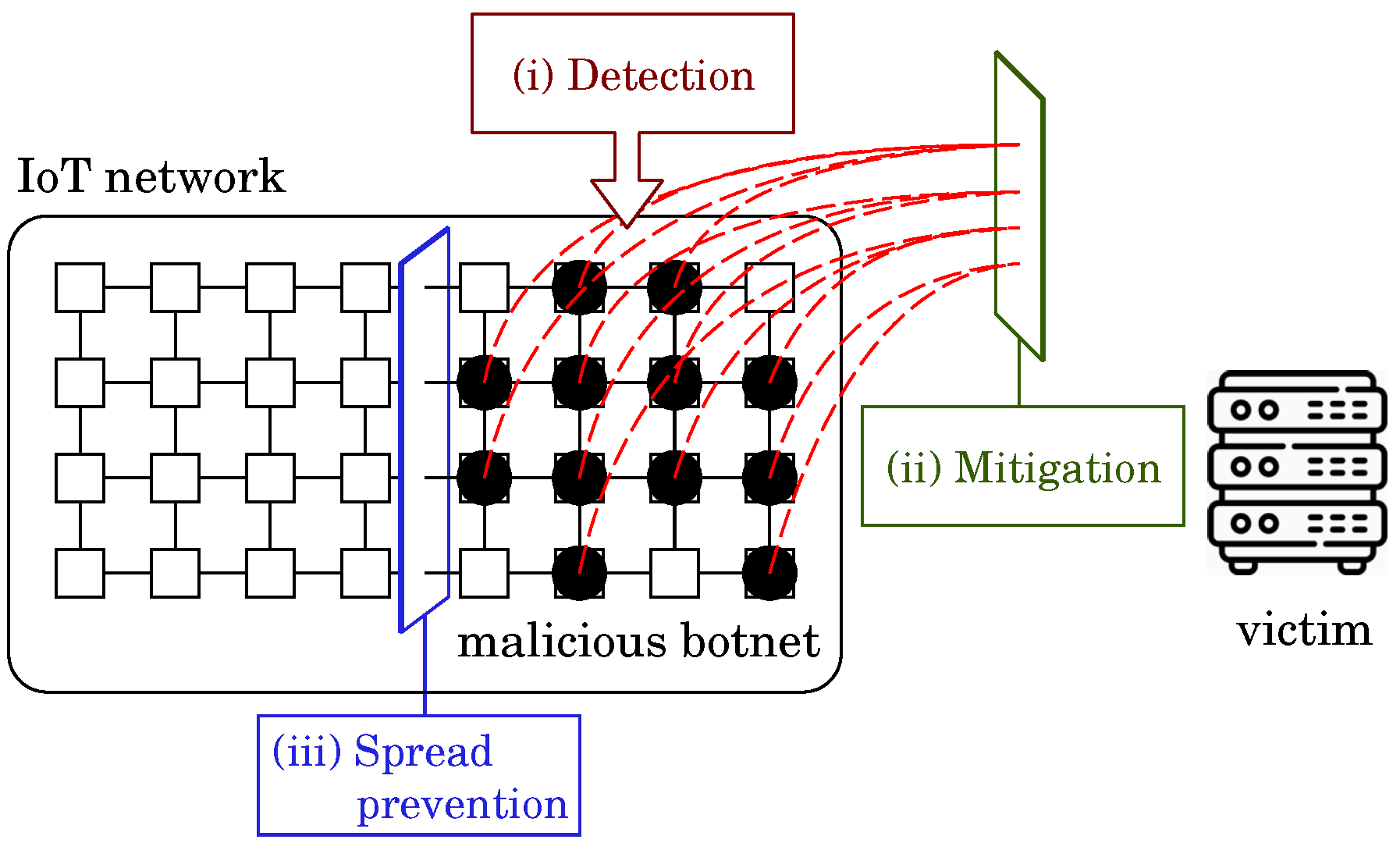
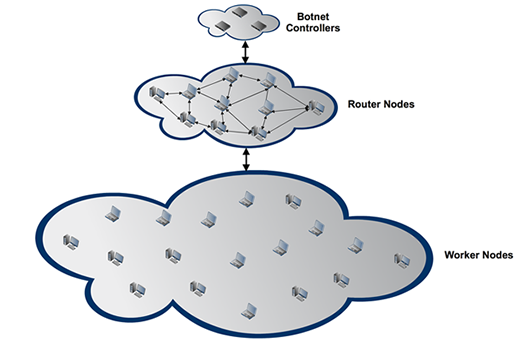
Sensors | Free Full-Text | Botnet Defense System: Observability, Controllability, and Basic Command and Control Strategy